You Can't Buy Zero Trust Security
By: Joe Costello & Kane Gyovai
Published: May 16, 2024
Introduction
Successful business outcomes are increasingly dependent on digital solutions. Nearly every organization on the planet has some core digital component. Even organizations with operational products and services that are inherently produced and delivered through physical interactions rely on digital technologies to not only improve efficiency but also to develop and deliver innovative ways of achieving objectives. It's a digital-first world. In a digital-first world, data and digital resources are indispensable resources.
Despite this transition, driven primarily through digital transformation, the tools and processes used to secure digital resources are often still based on traditional information security paradigms. The traditional way of doing information security is, at its core, based on the tenets of statically defined rules and network boundaries. In today's environment of complex network topologies, ubiquitous IP-enabled edge computing devices, remote work, identity federation, and the relentless pursuit of digital disruption by hackers and adversaries, traditional information security tenets are simply inadequate. As the digital attack surface grows with the rapid adoption of new digital tools and technologies, it is expected that cyberattacks will continue to increase in number and sophistication underscoring the urgency for organizations to strengthen and improve cybersecurity practices and capabilities.
Enter Zero Trust (ZT). The tenets of ZT were developed to provide levels of security and observability required for modern digital ecosystems. In this article, we describe these tenets, how ZT differs from traditional information security, how BridgePhase helps our customers approach ZT, and how ZT enables organizations to reduce risk and increase agility. Along the way, we emphasize the use of cross-cutting layers and the need to approach ZT adoption from the perspective of a journey rather than a set of boxes to check.

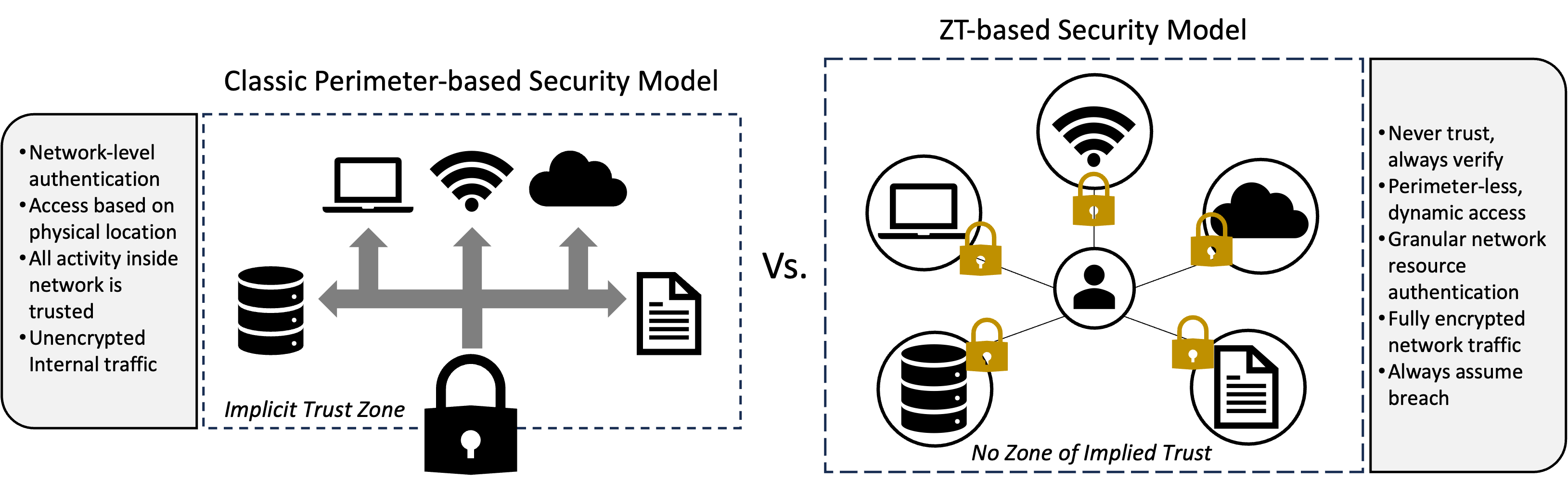
What is ZT and how is it different from traditional security?
As defined by Executive Order 14028, "Improving the Nation's Cybersecurity", the term "Zero Trust Architecture" is a security model, a set of system design principles, and a coordinated cybersecurity and system management strategy based on an acknowledgement that threats exist both inside and outside traditional network boundaries. This represents the fundamental difference from traditional, network-centric security approaches that do assume a level of trust within the perimeter of the network, believing that bad actors come from the outside. As such, these legacy models focused on keeping the perimeter secure, primarily concentrating on intrusion detection to adequately secure the organizational assets residing within the network. In contrast, Zero Trust does not assume any level of implicit trust for any devices or users, regardless of whether they are internal or external. Rather, Zero Trust Architecture prescribes a dynamic, granular, and data-driven access verification approach that evaluates each request in its entirety prior to granting access to any resources. This context-aware verification considers several factors such as identify, device health, policy compliance, and other aspects to ensure a holistic request evaluation is performed. Adopting this data-centric, least-privilege security approach moves organizations away from "trusted" network zones, reducing the potential attack surface, restricting lateral movement within the network, and strengthening the organization's cyber defenses.
Driving ZT Capabilities and Maturity
Zero Trust is not a single product or platform that you can buy, nor is it about pillars or checking administrative boxes; it is about securing organizational assets and information with a robust, dynamic, context-aware approach to cybersecurity. We understand that each organization’s ZT journey should be specific to their organization and that this journey does not have a fixed destination or finish line. Our approach to helping our clients achieve their ZT goals starts with an understanding of their needs, priorities, and current state. We help align these goals leading federal guidance and frameworks to define an achievable roadmap leveraging our expertise with Zero Trust platforms, tools, and technologies, resulting in the implementation and maturation of ZT-aligned capabilities to realize a secure, resilient, and modernized security architecture. With this approach, we enable organizations to extract the most value from their existing processes, resources, and technology ecosystem by applying ZT principles to incrementally adapt that foundation. For example, many DevSecOps best practices such as infrastructure-as-code (IaC) and ubiquitous automation, which are already being adopted by many organizations, can readily be applied to incrementally implementing ZT capabilities using our approach - which positions organizations for success by building on trusted solutions that have been proven to work for their environments and culture.
Maximizing the Use of ZT Frameworks and Maturity Models
While there is no one single path to realize a Zero Trust architecture, several useful models and frameworks have emerged that serve to guide and measure Zero Trust efforts. Our experience has shown that the true value of frameworks come when they are leveraged as guidance for these efforts rather than reducing them to a set of boxes to be checked for compliance or miscategorizing adherence to a framework as an indicator of success. When leveraged as resources to inform, guide, assess and measure progress towards achieving the objective at hand, these frameworks provide significant value. For our clients in the Federal space, resources such as CISA’s [Zero Trust Maturity Model](https://www.cisa. gov/zero-trust-maturity-model) (v2) and [DoD’s Zero Trust Reference Architecture](https://dodcio.defense. gov/Portals/0/Documents/Library/(U)ZT_RA_v2.0(U)_Sep22.pdf), amongst other resources, provide excellent sources of Zero Trust guidance and information. Through our work supporting ZT efforts across the Federal landscape, we have observed a pattern of agencies leveraging CISA’s model focusing on maturing the 5 pillars specified (identity, devices, networks, applications and workloads, data) but neglecting the cross-cutting capabilities such as visibility and analytics as well as automation and orchestration. Alternatively, those leveraging the DoD model that specifies 7 pillars, inclusive of visibility and analytics as well as automation and orchestration, has resulted in more focus and attention being paid to those cross-cutting areas. For these reasons, rather than trying to decide on “the right” model or framework, we help our clients realize the value in leveraging and incorporating the best aspects of the models and frameworks that are most effective in driving ZT progress forward in alignment with their specific agency needs and priorities.
Our Approach
While the case for moving to a Zero Trust Architecture is clear, achieving a ZT-aligned cyber footprint can be a bit more elusive. To help our clients optimize their ZT efforts, we collaboratively formulate a ZT roadmap that articulates the desired capabilities, target timelines, and key dependencies of the organization. This roadmap should consider the current state of the organization’s cybersecurity tools and capabilities as well as its existing gaps, high-value systems, and mission priorities. As neither fixed or finite, these roadmaps help communicate and validate an actionable path toward the realization and continued improvement of the organization’s cybersecurity resiliency in a ZT-aligned fashion.
While identifying a perfect starting point for your ZT efforts can be a challenge, a logical first step is to identify your protect surfaces, or the organizational assets that need protection. On the surface this may seem like a simple exercise but for many organizations, identifying these assets is not as straightforward as it may seem. This discovery process can often yield new and previously unknown information about assets that exist within the organization. When done correctly, this will also help inform the prioritization of ZT-related activities, prioritizing high value assets over those that are less critical. Another effective entry point can be to start with the organization’s existing cyber capabilities that may already align or can be readily configured to align with target ZTA capabilities. What is imperative here is understanding the underlying capability dependencies that are often prerequisite tasks or sub-capabilities that should (or must) be in place to realize the full benefits of these capabilities. Additionally, we find that organizations who have made enterprise progress in the area/pillar of Visibility and Analytics, have the significant opportunity to make more informed and targeted decisions, based on real organizational data. Having access to the log data that describes the actual activities, usage, and patterns happening on the network is extremely valuable information that can be used to drive prioritization and impact.
Another common ZT adoption pattern for many organizations is an identity-centric zero trust foundation. Represented as the first pillar in both CISA’s ZTMM and DoD’s ZT Strategy, Identity can serve as a logical starting point for organizational data and information requests. The ability to implement the use of strong, phishing-resistant multifactor authentication represents an achievable and valuable ZT milestone. In addition, given the relative maturity of this domain it is likely that the organization already has a foundation from which to strengthen and evolve their capabilities, including secure and centralized configuration management which helps lay the foundation for effective identity and access management. We also see that organizations who have made strong progress in the area of asset inventory management, typically in the form of an accurate and current CMDB, have laid a strong foundation for progress to make meaningful progress in securing their devices and assets. Regardless of where your initial areas of focus for your ZT efforts lie, prioritization should be given to horizontal integration across the pillars over vertical maturity within a single pillar. Each of these pillars or areas have a key role to play in securing the assets of an organization, so it is important to avoid neglecting any of them and critical that the capabilities within each area can work in concert with each other.
Navigating Your ZT Journey
Each organization’s ZT journey will and should be unique. With any journey, to get to your target destination in the most effective way, you have to know where you are starting from. Our experts help guide our clients through this journey, helping them advance ZT capabilities and improve cyber resilience based on the unique attributes, priorities, and mission objectives of each organization. As you navigate your ZT journey we hope this article provides some guidance and enough foundational context to inform discussions and strategy within your organization. Regardless of your starting point, it’s important to remember – You Can’t Buy Zero Trust!
Want to learn more? Contact us.